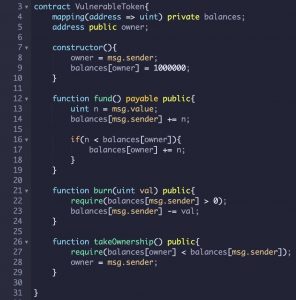
Contract Vulnerability Detection
Smart contracts can suffer from vulnerabilities that can be exploited by malicious entities. There are several methods for detecting smart contract vulnerabilities. One of these methods is called AttackerAgent, which can be used to identify reentrancy vulnerabilities. Once this vulnerability has been detected, an attacker can use it to attack other smart contracts, stealing ETH from them.
The existing vulnerability detection methods for smart contracts are inefficient and labor-intensive. Most of them use rigid rules defined by experts, which are unscalable, error-prone, and not suitable for large numbers of contracts. Furthermore, they do not account for extensibility of smart contracts. To combat this issue, researchers are working to create a more flexible and effective system.
The ESCORT vulnerability detection framework is the first DNN-based vulnerability detection framework for Ethereum smart contracts. ESCORT leverages a multi-output NN architecture to perform lightweight transfer learning for unseen security vulnerabilities. The NN framework consists of a common feature extractor and multiple branch structures. Each branch is trained to detect a particular vulnerability type based on features. ESCORT has been tested against six different vulnerability types and achieves an average F1-score of 95%. Moreover, detection time is as low as 0.02 seconds per contract.
Smart Contract Vulnerability Detection
A preprocessing module consists of four steps: generating fuzz test inputs, defining test oracles, recording run-time state of smart contracts, and analyzing the log. It can also report security vulnerabilities through Ethereum Virtual Machine instrumentation. Its tools include an offline EVM instrumentation tool, which allows fuzzing tools to monitor smart contract execution.
The EtherFuzz framework is another method for smart contract vulnerability detection. It uses mutation fuzzing to detect TOD vulnerabilities. The framework identifies a TOD vulnerability by using test data that has been generated by smart contracts deployed under test. It also generates new test data covering new branches, minimizing the false-positive rate. The EtherFuzz framework also significantly reduces detection time. It also offers a low false-positive rate, and can be used for larger smart contracts. It is especially suitable for detecting security problems in the Internet of Things.
As the number of smart contracts increases, the security of these contracts is becoming a major concern. Recent hacker attacks have led to significant losses for the blockchain community. One example was the DAO security breach, which resulted in a loss of $60 million US dollars. A similar vulnerability also affected the Parity wallet, causing the freezing of $150 million worth of Ether.
While there are several smart contract vulnerability detection algorithms available, there are two that are especially suitable for smart contracts. EtherFuzz has a low false-positive rate and reduces detection time and memory overhead. Furthermore, it is a highly efficient tool, which means that it has a high application value.